Sextortion – Don’t be a victim!
Share this:

Sextortion is a sensitive subject AND now is one of the top three online scams that people need to be aware of. Trust me it happens! I have assisted three clients with this over the last year. Cybercriminals use sextortion mostly to exploit victims to extort money, or blackmail. A sextortion attack usually originates by an email from a hacker who threatens to release embarrassing personal images/video to the victim’s contacts and/or publicly.
While it is possible that the compromising images may come from the victim’s webcam or phone camera, the vast majority of these are a scam. Sextortion hackers are trying to get you to believe they have this information and make you pay the ransom without any verification.
However, if the incident is real, the perpetrator will have damaging photos and/or videos. These could have come about in a variety of ways:
- Social media
- Phishing emails
- Messaging apps
- Online dating apps
- Hacked online accounts
- Hacked webcams (personal recordings or secretly recorded)
- Your mobile device via malware that was downloaded from a bad app, game and/or open WiFi
With sextortion crimes at an all-time high, it’s important to know what to be aware of. The majority would hope they wouldn’t fall for such scams or get hacked in that way. Unfortunately, such plots happen daily. Statistically, of all the online crimes in the USA, romance scams add up to one of the largest financial losses. It’s also happening in other countries. The UK and Canada are hard hit as well. It is likely that a majority of victims are too embarrassed to come forward and as a result, the total numbers may be vastly underreported.
Since recovering monies sent to a sextortionist is nearly impossible, there is a light at the end of the tunnel. Educate yourself, family and others about tactics these type of cybercriminals use to scam people and businesses to significantly reduce the chances that you or they will become a victim.
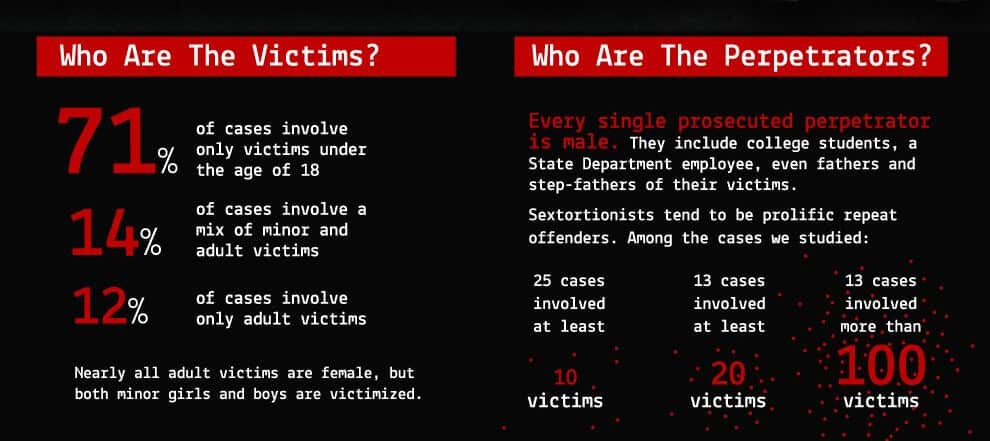
Source: comparitech.com
Here are some common tactics used by scammers and then how to avoid getting caught up in their scams.
Recognizing Red Flags

- The subject line of the email may read, “I have full control of your device”, “Busted” or “I have videos of you in a compromised situation.”
- The sender’s email address is usually unknown.
- There is no offer of evidence to prove the cybercriminal has the information they claim.
- The criminal asks for an urgent ransom be paid in gift cards or bitcoin.
- The message includes grammatical errors, instructions for payment and a window of time in which to comply.
- Below is one example of a sextortion email; however, attackers frequently prepare spam campaigns in accordance with current trends and events.
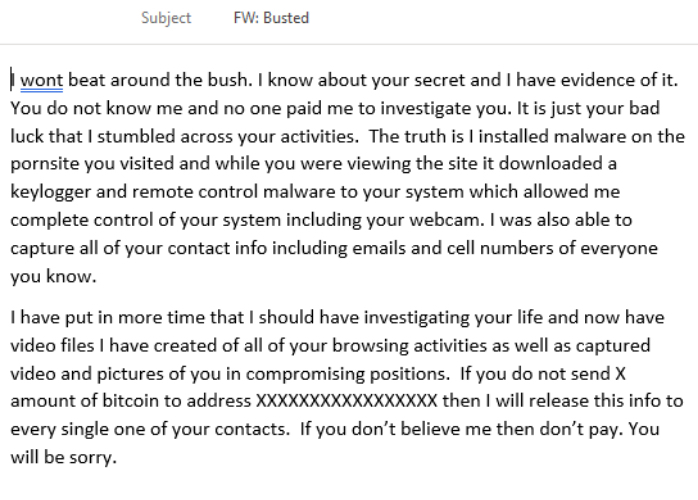
How to protect yourself
- You can copy and paste the entire message into Google to see of any similar scams pop-up. If you see exact matches, then there is a 99.9% chance it is a scam.
- You can also copy and paste the Bitcoin address (X’d out in the above example) on https://checkbitcoinaddress.com/. If this bitcoin address is used in other scams, it will most likely be listed here.
- Never send compromising images/video of yourself or anyone else to anyone regardless of who they say they are such as on dating sites, social media sites, etc.
- Do your due diligence and find out who you are talking to. Scam artists create fake profiles a/k/a “catfishing” to lure in their prey. Some even use the same photo and different names. This is a site that could help with research: https://scamdigger.com/.
- Do not download games and apps before investigating them first.
- Do not connect to open hotspots nor free WiFi.
- Do not respond nor pay the demanded ransomware. Delete the email or text.
- Do not click on any links or attachments in the email. Have an IT professional review the email if needed. That link or attachment could have malware in it too.
- Monitor your children’s online activities.
- Check to make sure your email address(es) has not been involved in a data breach on a site such as haveibeenpwned.com.

- For peace of mind, turn off webcams or cover the camera on your computers, laptops and all other mobile devices while in private spaces.

Keith Coker, President/Partner
If you encounter cybersecurity issues relating to sextortion, we can help with your company’s unique demands. Connect with a Client Success Manager to schedule a time to discuss your needs and how we can meet them.
Make IT Work
-
Talk with an OrlanTech expert
-
Discover reliable advice and fast support
-
Be safe, secure and productive




