Ransomware – What to do when you are attacked
Share this:
Ransomware Attack
“Ransomware is defined as vicious malware that locks users out of their devices or blocks access to files until a sum of money or ransom is paid. Ransomware attacks cause downtime, data loss, possible intellectual property theft, and in certain industries an attack is considered a data breach,” as defined by KnowBe4.
History
Over the years, ransomware has evolved. In the history of the Internet, never before have people around the world been more subjected to coercion on the massive scale than they are today. This is as a result of greater online access and with its massive growth, cyber criminals are targeting users with a range of malicious malware with the sole intent of making money from their victims. Nowadays, ransomware is one of the most worrisome malware categories known.
Although you hear more and more about ransomware attacks today, they have actually been around for 20 years as of this writing. They have been and continue to be a genuine threat to corporations, public agencies, SMBs and individuals since the mid-2000s. The first of modern ransomware was in 2005 and named the Trojan.Gpcoder.
Most modern day ransomware targets personal computers, mobile devices and servers. As computerization advances, however, many types of systems can potentially be targeted with ransomware. The IoT has already broadened the scope to portable media players, routers, refrigerators, TVs, set top boxes, network-attached storage (NAS) devices, USBs, surveillance cameras and more. Insofar as countries affected, the USA leads the chart at 38%.
Current Statistics
It is evident ransomware is definitely making its mark.
- Attacks that demand payment to unlock files: 51%.
- Incidents caused by clicking on a phishing email: 65%
- Percentage caused by visiting a malicious website: 35%
- Percentage of large businesses impacted by ransomware: 15%
- Approximate number of individuals who lost files to ransomware in 2018: 600,000
- Number of new forms of ransomware in the first four months of 2019: 25M
- Hacks caused by theft of passwords and user names: 63%
- Attacks caused by
- opening an infected Microsoft Office document: 38%
- opening an infected .zip file: 37%
- opening an infected PDF: 14%
- Victims who paid the ransom and hoping, not guaranteed, to get their files back: 45%
- Those who paid the attackers but did not get their data back: 40%
Sources: CISCO, Microsoft, Imperva, ENISA, AV Test
Facts
A new organization will have fallen victim to ransomware every 14 seconds in 2019, and every 11 seconds by 2021, according to cybersecurity Ventures. If a ransomware attack were to occur in your business or organization, there would be direct, indirect and hidden costs.
- Direct costs – lower sales revenue, which would affect operational activities and business productivity; hence causing the company’s share price to drop. Legal fees to control litigation cases, and additional costs if investigative consultancy firms are needed to explore the root cause of the data breach. Add more costs for implementing a post-breach response for affected customers and the possibility of other activities that could include financial reimbursement or settlement costs to impacted customers. Lastly, large amounts of money to pay fines.
- Indirect costs – a damaged reputation, loss of consumer trust and missed business opportunities; hence causing the company’s share price to drop. Loss of talented employees who may leave the business due to reputation declines. Third-party costs, such as business insurance, cloud service providers bolstering cybersecurity, other suppliers, etc.
- Hidden costs – lost business hours as employees try to resolve the breach, rebuild systems and recover data. Plus, additional monies would need to be spent on future technology investments and training.
How It Spreads
Hackers use various courses to spread ransomware by means of phishing emails, messages, popups, vulnerable ports, unpatched software, social engineering, compromised websites with ads (malvertisements) or free software downloads.
Not only can ransomware encrypt files on an individual’s computer, but it can also be designed to move through connected drives and devices. When a network is breached, the hacker often uses other malware to gain lateral access to different parts to implant ransomware more broadly.
If victims choose to pay the ransom, it is with cryptocurrency, usually Bitcoin. Procuring cryptocurrency is not easy. Hackers give instructions; however, with ransomware attacks as common as they are now, there are more financial institutions that can secure Bitcoin, as well as IT security professionals who will manage your ransomware incident response.
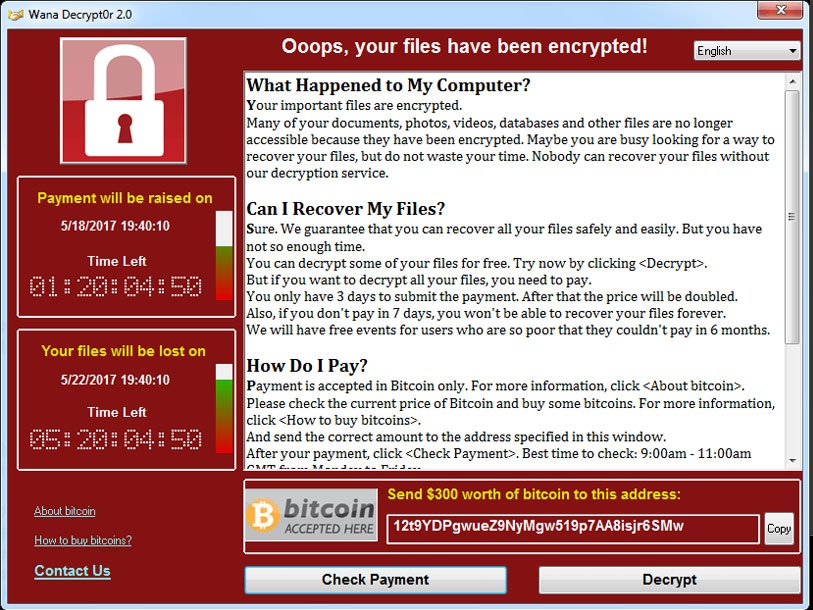
What to Do Next
When ransomware strikes, stop it from spreading immediately and follow these steps.
- Train employees to report it to IT the moment they see it. Many are reluctant to do so for fear of having to admit it was their error and would then be responsible for the ransom.
- Physically disconnect the machine from any others and the network it is attached or mapped, and any external drives. Turn off wireless connections also.
- From the ransom message, computer evidence and ID tools, determine which strain of malware you are infected.
- Take a photograph of the ransom note on the screen to file a police report later.
- Lock down the network.
- Inspect all machines and data stores on the network, including all backups and all cloud storage.
- Compare encrypted data to that which is backed-up to determine the loss, if any.
- Check your operability to assess the damage and where you stand internally and externally.
- Determine your options: use a decryption tool and try to decrypt your data without having to pay the ransom; negotiate and pay the ransom; try and remove the malware; or wipe the system(s) completely and reinstall from scratch.
- Assess how it happened and what measures can be put into place to ensure it does not happen again.
If You Decide to Pay Ransom
If critical data was encrypted and there are no backups, most likely negotiating and paying ransom with the hacker may be in order. If this should be the case, a trained incident response professional can streamline and improve your recovery. It is important to note this is no sure guarantee you will recover your data; however, nowadays there is a much greater chance (95% – 98%) you will. After all, hackers have a reputation to maintain!
Now on the other hand, if you have viable backups, communication with the hacker is not at all necessary. Just wipe your system completely and reinstall everything from scratch, including your backed up data.
Closing
Realizing the magnitude of a ransom attack, you need to be aware of how they happen and how to prepare in advance and respond afterwards — should it happen to you. Not every battle will be won, so be vigilant about good backups at all times in the event an incident occurs. Caveat, just because you have been held hostage once, doesn’t mean it won’t happen again.
Be aware the majority of attacks are caused by human error either by clicking on a bad link or attachment in an email, message or on a website and/or having poor passwords. Technology helps, but it will never win this war. Changing behavior with training and education are necessary to help control poor decisions. Be aware and careful in your online activities to do your part to stave off cyber criminals in your business and at home.
Make IT Work
-
Talk with an OrlanTech expert
-
Discover reliable advice and fast support
-
Be safe, secure and productive




